Let me start with an allegedly ancient saying.

Today, we will not be teaching a man to fish or be giving anyone fish. But we will discuss “spear phishing.” Huh?
While spear phishing and phishing have the similar techniques and the same result in mind--to convince a user into opening an attachment or to click on a link that has malicious code embedded-- spear phishing is even nastier.
Fish, Phish, Splish, Splash -- say it fast four times
Phishing typically explores a broad audience (sort of along the lines of, “Who is stupid enough to do XXX or click on YYY …?” And, sadly enough, that stupidity factor is high). Once phishing gets the bank account information or the social security numbers or whatever it seeks, the main event essentially ends and the collected data is sold or used for other immediate nefarious purposes.
Spear phishing generally happens over time. It is normally not a “once and done” event. The initial theft of account numbers, credentials, etc. is just the start of a much larger and more pervasive (normally corporate) attack.
I recently received an email addressed to only me, from a company where I work as a consultant. It was from the HR Director, with whom I regularly communicate, and it asked me to click a link to confirm some data. I sensed NO issue. But it was a spear phishing attempt that, fortunately, was not very well executed and the I/T department was able to stop it almost immediately.
These spear phishing attacks are easy to stop, right? And spear phishing doesn’t really adversely affect big companies, correct? Wrong and wrong.
WHOOOOOO GOT SPEAR PHISHED?
In March of last year, two companies you might have heard of experienced spear phishing attacks: Facebook and Google. What?? Well, we’re actually just pretty sure, and we THINK the two companies were Facebook and Google, and we are fairly certain they won't really discuss it in public.
In Fortune’s, “Exclusive: Facebook and Google Were Victims of $100M Payment Scam,” read the intrigued-laced first paragraph of the article:
“When the Justice Department announced the arrest last month of a man who allegedly swindled more than $100 million from two U.S. tech giants, the news came wrapped in a mystery. The agency didn’t say who was robbed, and nor did it identify the Asian supplier the crook impersonated to pull off the scheme.”
So what happened and why was it not reported? Working backwards, both companies eventually got most of the money they lost returned to them. And, if this had been reported, it surely would have initiated a major and ugly report to investors and all of the ramifications that involves. So, since they got the funds back, no harm no foul right? Ummm …..

Here’s how it worked. A Lithuanian named Evaldas Rimasauska forged email addresses, invoices, etc. in order to impersonate a large manufacturing company from Asia that both firms regularly used to supply them with computer equipment.
“Over a two-year span, the corporate imposter convinced accounting departments at the two tech companies to make transfers worth tens of millions of dollars. By the time the firms figured out what was going on, Rimasauskas had coaxed out over $100 million in payments, which he promptly stashed in bank accounts across Eastern Europe.”
Clearly, then, no company is immune to these scoundrels. And, by the way, I have always loved the word scoundrel as it reminds me of Fabio-on-romance-novel-covers impersonating Robin Hood, stealing from the rich to give to the poor while riding a white horse. Yes, I have a warped mind. And I digressed. Apologies.

“NO PHISHING” SIGNS MUST BE POSTED
So what in the world does all of this have to do with the mortgage industry? Oh come on -- large batches of personal data, inconsistent tech security, endless scoundrel possibilities? Of course the mortgage industry will be phished, fished, speared and spear fished.
From Credit Union Times, “Anatomy of Mortgage Spear-Phishing Campaigns” Cyber criminals are taking advantage of the new home builds and sales by hacking into accounts through email.
From Multihousing News, “Avoiding the Bait of Spear-Phishing Scams”
According to Symantec, the real estate industry is one of the top three targeted for spear-phishing attacks, and real estate executives are the catch of the day.And from Security Week, “Mortgage Phishing Scams Target Big Payouts”
Over the last few years, business email compromise (BEC) scams have rocketed -- costing victims $1.45 billion in 2016 alone (FBI report). Now a new related threat has emerged -- the mortgage phishing scam -- that seems likely to follow a similar trajectory.And these examples go on and on and on ...
Good grief. Can someone/anyone please explain to me why these talented techno people choose to filch companies and create evil instead of using their talents for the good of the world? And, yes, I just pretty much quoted my dad there, from twenty years ago. OH NO!!! I’m suddenly in need of Progressive Group Therapy!!!! (Sorry, but that is one great ad if you are of a certain age … mine, ha.)
I don’t usually digress twice in one blog. So sorry. 🙂

BARRELS OF PHISH
Back to spear phishing and the mortgage industry … According to mortgagetrainers.com,
- 1 in every in 2.3 lenders is targeted by a spear phishing attacks.
- $600,000 is the average cost to repair damage done by one spear phishing attack.
In these days of tight margins, mortgage companies will think twice about spending over half a million dollars to clean up after a cyber attack. And that does not include the direct and immediate loss of funds caused by this type of spear phishing attack.
Mortgage compliance magazine recently posted a sample email that displays spear phishing.
JOHNNY I HARDLY KNEW YE
Imagine some party to the transaction receiving this email below. Why would they ever think to challenge it? It came directly from someone they had already been working with on email -- same name, same email address .... And lots of companies change banks lots of times. No red flags whatsoever.
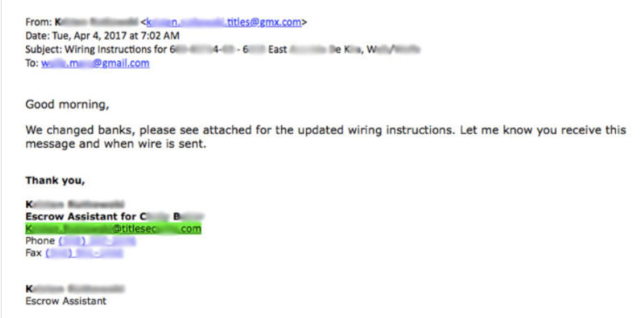
And just like that, funds were wired to an account that will cease to exist seconds after this money arrives. Major red flag to all lenders.
HOW TO KILL THESE PHISHES

What exactly should mortgage companies do to ensure the phishing supply ceases to exist? First of all, they can try the old out source method. There are veritable fish farms of phish firms available, but not for free. (Yes, I tried to fit as many F words there as possible! And, on that note, why isn’t phonetic spelled fonetic?) Onward …
Check out the names of the first three Google listed phishing cessation firms:
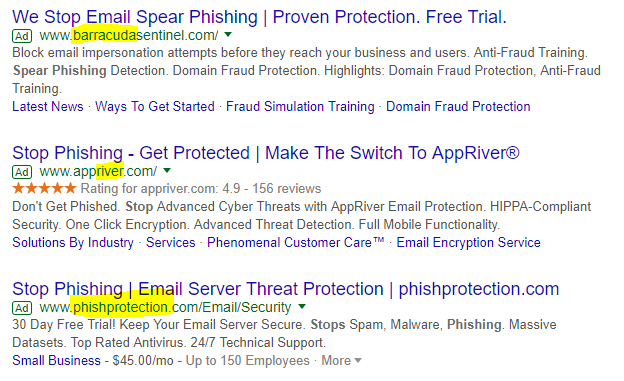
We are definitely having fun now! But what if a firm chooses not to fork over phishing fees? (Okay I’ll stop now.) What steps can be taken to lessen the attacks?
TEACH A MAN TO STOP PHISHING
Cyber defense company’s site Fireeye.com supplied an entire white paper on that topic, “Best Defense Against Spear Phishing.” They also supplied similar reports such as “Top words used in spear-phishing attacks” and “Advanced security for cloud based email services.”
CIO.com provides, “How to stop spear-phishing cold.“ I am pasting a short paragraph from their site here as I found it hugely informative and interesting (and confirmation that I am, in fact, a weirdo).
“... a whole family of attacks called Internationalized Domain Name (IDN) Homograph Attacks, in which, for example, a Latin “i” is replaced by a Cyrillic “i,” or a Latin “B” is supplanted by a Cherokee letter that looks identical. Thus, even an expert scrutinizing the address bar of a domain visually could not detect this type of spoof. But underneath that masquerading Cyrillic “i” is an entirely different string of bits, leading who knows where.”

In a blog at barkly.com, “5 Tips for Keeping Users Safe from Spear Phishing,” the advice was:
1)Remind users to always hover over hyperlinks to see the destination URL first. It that is not familiar, do not click it.
2)Contact the sender if something does not look or feel right about an email. If the sender denies sending, contact I/T.
3)Make it a practice to never send confidential and to alert I/T for all requests to do so.
4)Post as little personal information online as possible. Do not post work phone numbers as phishers often call masquerading as coworkers and requesting personal information “safely” via phone.
5)Use a behavior-based endpoint protection too instead of signature based. Huh? Per Stack Exchange,
“Signature-based AV compares hashes (signatures) of files on a system to a list of known malicious files. It also looks within files to find signatures of malicious code.
Behavior-based AV watches processes for telltale signs of malware, which it compares to a list of known malicious behaviors.
The reason many AV products are add behavior-based detection is because many malware creators have begun using polymorphic or encrypted code segments which are very difficult to create a signature for. An easier way to detect these is to watch for a particular pattern of behavior to identify the malware.”
In short, then, mortgage and other companies and their I/T departments can self-teach using web based tools, or outsource the protection to experts, or clean up the fish scales afterwards. Whatever they choose, it is definitely time for some levity!




And finally … Why did the computer sneeze?
It had a virus
Now I’m, of course,























